A Summary of 6 Months Tracking AiTM Campaigns
About 6 months ago Lab539 devised a technique for identifying Adversary in The Middle (AiTM) infrastructure in real time before it is fully weaponised and used in attacks (we’ll share a bit more detail on how in a future post). It has been fascinating to watch these attacks materialise and see who is being targeted so this post shares a little of what we have seen.
The rise in AiTM being used for account compromise has ramped up significantly, heavily driven by a surge in multi factor authentication roll outs - it's no longer sufficient to simply capture credentials, but the adversary must also now circumvent whatever MFA controls are in place too. Fortunately for adversaries many widely used MFA solutions, such as Microsoft Authenticator, are not phishing resistant and so we'll no doubt see these attacks continue for some time to come until stronger MFA is commonplace.
Very brief background done, let’s start by plot a snapshot of some of the recent activity we have seen:
IP to Domain Mappings
Here the orange dots represent an IP address and blue dots represent a domain. We can see, for the most part, infrastructure is not shared amongst campaigns. Most domains are hosted on their own infrastructure and infrastructure is mostly not re-purposed. This aligns with the transitive short-lived nature of phishing campaigns that we see these days.
The exceptions to this appear in the top part of this diagram where we start to see single IP addresses hosting multiple domains. In most cases, even where a single domain is in use, we see multiple DNS records pointing to the same IP. This is because the vast majority of the attacks we saw were directly impersonating already existing infrastructure and so had DNS records that replicated that as closely as they could. When we balloon things out to include all DNS records for the same time period things look even busier:
IP to Hostname Mapping
In this diagram the brighter orange dots represent an IP address with the darker dots representing a DNS entry that points to that IP address. Typical subdomain labels that we see are things like "outlook", "login", "sso", "okta", "account"... you get the idea.
The vast majority of targeting we saw was generic, looking to capture credentials or access accounts on a more widespread basis. It’s what you’d expect the activities of initial access brokers or groups focused on business email compromise to look like; generic targeting.
Obviously Microsoft accounts were right up there as the most targeted, but Google accounts and other likely suspects were certainly there too, as were social media account, cloud hosting administrative accounts, and those which might be tied to source code repositories. We also saw some targeting of open-source projects and targeting of cloud providers themselves - not just their users. The social media side of things was interesting too - whilst there was a lot of general social media targeting, we also saw some instances where a single piece of infrastructure impersonating, for example, a crypto currency platform login page also presented a Google authentication page. Clearly adversaries have recognised that users like to authenticate to multiple platforms with a single account and if someone’s crypto is behind their Google account, then that is the authentication you need to be proxying!
The creativity of some campaigns was quite exceptional, it certainly didn't hold true the entries with multiple domain or subdomain to IP address mappings were the most interesting. In fact, a particularly interesting instance that we followed targeted several major US financial institutions. The campaign ran for most of January 2024 and appeared to have been targeting contractors or remote workers of these organisations. If we plot the domain to IP address mapping there is not much to it, a single domain and a single IP address:
Domain to IP mapping of banking campaign
If we plot the subdomains, then we get something a lot busier, as several subdomains were present for each target organisation:
Subdomain to IP mapping of banking campaign
The adversary had clearly spent time exploring their targets infrastructure and used this to inform their approach. The presence of the names of their victims in the domain labels tell us that this was a very targeted campaign which is what made it stand out to us. We don't know if it was successful, but it ceased after a month of operation and the domain appears to have changed hands since.
Another campaign that jumped out as interesting to us is this one:
Linked infrastructure of fast food campaign
This specific campaign was and remains persistent. We have observed it targeting the fast food sector over a period of at least 3 months with the infrastructure moving between multiple different countries as different food outlets were impersonated. It's not one that we tracked too closely at the time, but we assume that the intent was to capture payment card details or gain access to online payment accounts (e.g. PayPal) of customers using these platforms rather than in targeting the outlets themselves.
Interestingly the adversary here did appear to align the hosting of their infrastructure with the region that they were targeting and made it easier for us to follow their activities because their infrastructure occasionally overlapped (as you can see in the graph above) allowing us to link it without any real effort. The map above only represents a small portion of the infrastructure operated by this group. Despite the majority of their infrastructure appearing to be single use with no overlap, other hallmarks of their campaigns allowed for their infrastructure to be linked to them with a high degree of confidence. We hear very little about cyber security in the fast food sector, but if there is anything that we've learned watching these campaigns is that the attacks are occurring across most sectors, not just within the usual suspects.
So that was a brief intro to some of what we've been seeing, but we couldn’t wrap up without a few stats and answers to questions:
Which organisation/sector/company are most targeted?
Microsoft accounts, not Microsoft specifically, but Microsoft 365 accounts are most targeted by a significant margin. So, anyone using Microsoft 365/Azure falls into that bracket.
Sample Microsoft phishing site used by one of the tracked campaigns
Which country have we seen hosting most AiTM infrastructure?
The chart below shows the top five countries hosting AiTM infrastructure according to our data:
Top 5 AiTM hosting countries
The US comes out on top in this one, which is probably unsurprising, since the US is both most targeted and is also home to most hosting infrastructure. Netherlands is there because, as any defender knows, the bad guys like to host their stuff there for reasons... Germany, the UK and France likely get their scores because adversaries prefer to use infrastructure in the countries which they are targeting.
Which hosting providers have we seen hosting most AiTM infrastructure?
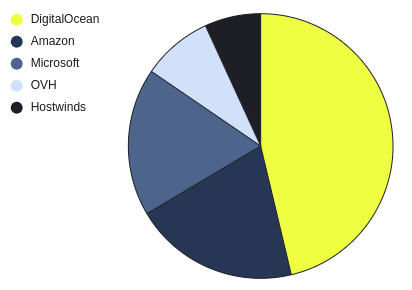
This chart shows the top five hosting providers hosting this infrastructure according to our data:
Top 5 AiTM hosting providers
No, DigitalOcean coming out on top didn't surprise us either, but Amazon and Microsoft did a bit. Obviously they both make sense, they are considered reputable hosting providers and a Microsoft login page on Microsoft infrastructure is less likely to raise suspicion than one hosted elsewhere. Equally AWS is obviously extremely widely used, so offers the opportunity to blend into existing infrastructure. Please note that these stats relate to backend infrastructure (i.e. where the proxying is taking place rather than the front-end where the phishing sites might be presented - which is the reason that Cloudflare does not make an appearance).
Which registrars are adversaries preferring for their domain name registration?
These are the top 5 registrars of choice for adversaries carrying out AiTM attacks according to our data (i.e. the companies that are being used to register the domains that these attacks use):
Top 5 AiTM registrars
NameCheap takes that crown by some margin, not a new theme, and probably not a surprise to anyone working in cyber defence. The full list of registrars who have been used to buy domains for AiTM purposes was quite long, but the quantity of domains against each registrar tailed off into single digits after the first ten or so registrars.
This is very cool, but did you have to burn my Red Team exercise?
Lol, sorry! Take it as a sign that your tradecraft was close enough to that of a real adversary and that your target was an organisation we felt a duty to inform. It's extremely rare that we reach out directly to targeted organisations, so you just got very unlucky. Get in touch and maybe we'll sort you a T-Shirt (offer also available to real adversaries too!).
Can I integrate it into my defences/tool/etc.?
Yes, probably, get in touch. At the moment we’re rolling out a beta that integrates with Microsoft Conditional Access policies so that you can block authentication from all of the infrastructure that we have collected. But if you have another use case, at the end of the day it’s a feed of IP addresses (and/or domains), so drop us a message I’m sure we could figure something out.