The vast majority of successful attacks that Lab539 observe relate to credential theft. A large proportion of these now also bypass multi factor authentication controls such as Microsoft Authenticator.
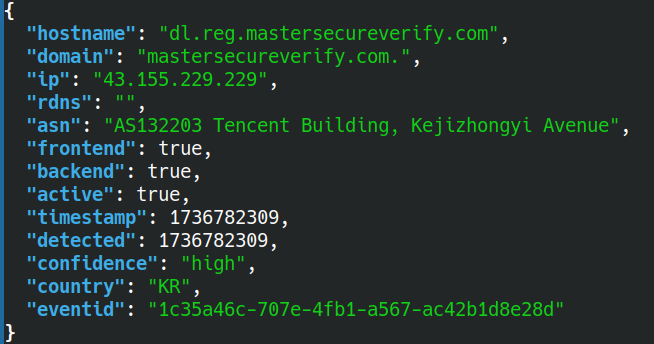
To mitigate these attacks we created some rather clever (and we believe unique) capability to detect and block the infrastructure which will be used for these attacks before it has even been fully deployed, and usually long before the attacks start. This is not a feed of IP addresses that have been observed carrying out nefarious activities, this is a feed of infrastructure that is are about to carry out nefarious activities. We proactively detect Evilginx and other front and back end AiTM infrastructure and provide high quality Indicators Of Attack (IOA) enabling you to disrupt adversarial activities targeting your environment
High quality data accessible via our API
Multiple Microsoft named location and Defender Indicator feeds. Updated in near-real time.
“The cornerstone of the Lab539 AiTM feed’s value is its unique ability to identify malicious Adversary-in-the-Middle (AiTM) infrastructure before it becomes actively engaged in attacks.
This fundamental difference distinguishes it from conventional threat intelligence, which typically relies on there being victims from whom indicators of compromise (IOCs) can be identified.”